Which type of software enables centralized administration of mobile devices is a question that sparks curiosity in the fast-paced digital world where organizations strive to manage countless smartphones, tablets, and laptops. From small businesses to global enterprises, the challenge of keeping data secure while maintaining operational efficiency is universal—and that’s where centralized management software steps in as a game-changer.
Centralized software platforms enable IT teams to control, configure, and secure mobile devices from a single dashboard, ensuring that every device connected to the network meets compliance standards and company policies. These solutions not only streamline device enrollment and enforce security protocols but also support integrations with other IT systems to create a unified, scalable, and efficient approach to device management. Whether it’s Mobile Device Management (MDM), Enterprise Mobility Management (EMM), or Unified Endpoint Management (UEM), each type brings unique features and integration capabilities to meet diverse industry needs.
Centralized Administration of Mobile Devices: A Comprehensive Guide: Which Type Of Software Enables Centralized Administration Of Mobile Devices
Managing mobile devices across an organization can quickly get complicated, especially as the number of users, device types, and security requirements grow. Centralized administration software provides a streamlined solution to manage, monitor, and secure mobile devices from a single platform, offering organizations significant benefits in efficiency, security, and compliance.
Centralized administration combines technical controls and administrative policies to help IT teams support diverse mobile environments, enforce security standards, and maintain regulatory compliance, all while reducing overhead. This guide explores the key concepts, software types, features, and best practices involved in centralized mobile device management.
Overview of Centralized Administration for Mobile Devices
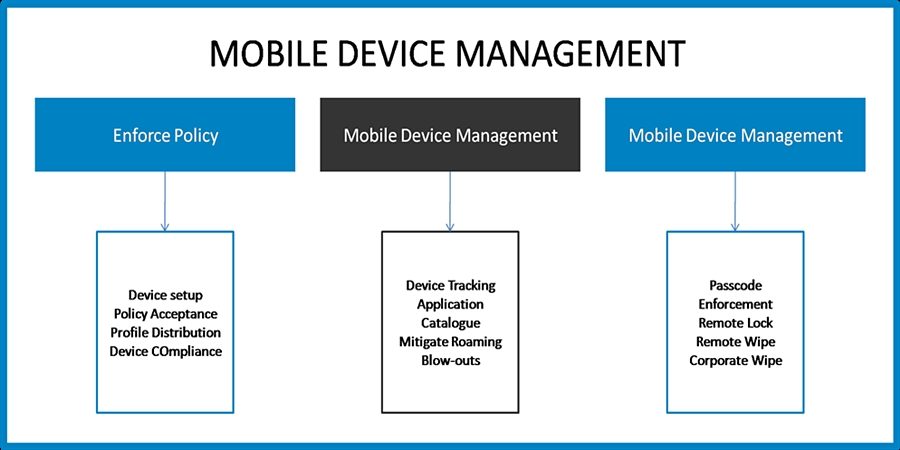
Centralized administration in the context of mobile device management (MDM) refers to using a unified system or software to oversee, configure, secure, and support mobile devices throughout an organization. Rather than managing devices individually, IT teams use centralized tools to automate and enforce consistent policies across all devices, regardless of location or ownership model (corporate or BYOD).
This approach is critical for organizations because it allows for scalable management of devices, rapid response to security incidents, simplified compliance processes, and more efficient troubleshooting and support. It empowers organizations to maintain control and visibility as their device ecosystem expands.
Types of Software for Centralized Mobile Device Management
Organizations use several categories of software to achieve centralized mobile device administration. These solutions differ in their scope, feature sets, and deployment methods. The following table compares the main types:
| Software Type | Main Features | Supported Platforms | Deployment Method |
|---|---|---|---|
| Mobile Device Management (MDM) | Device configuration, remote lock/wipe, inventory, policy enforcement | iOS, Android, Windows, macOS | Cloud-based, On-premises |
| Enterprise Mobility Management (EMM) | Includes MDM features plus app management, content management, identity management | iOS, Android, Windows, macOS | Cloud-based, On-premises |
| Unified Endpoint Management (UEM) | Manages all endpoints (mobile, desktops, laptops, IoT), advanced analytics, automation | iOS, Android, Windows, macOS, Linux, IoT | Cloud-based, Hybrid, On-premises |
Each type offers a distinct scope of management, with UEM representing the most expansive and integrated option for overseeing not just mobile devices but all endpoints within an enterprise network.
Mobile Device Management (MDM) Solutions

MDM solutions are dedicated platforms designed for managing mobile devices throughout their lifecycle within an organization. Core functions include device enrollment, configuration management, enforcing security policies, asset tracking, remote device actions (like lock or wipe), and facilitating software updates.
Some popular MDM platforms include:
- Microsoft Intune
- VMware Workspace ONE UEM
- Jamf Pro
- IBM Security MaaS360
- MobileIron (now part of Ivanti)
MDM solutions provide a robust set of security and policy enforcement features that help organizations minimize risks associated with mobile devices, such as:
- Enforcing device-level encryption requirements
- Restricting access to corporate resources based on compliance status
- Automating OS and application updates
- Remote wipe or lock in case of device loss or theft
- Application whitelisting or blacklisting
Enterprise Mobility Management (EMM) Platforms
EMM platforms extend the capabilities of traditional MDM by integrating additional components that address a broader range of mobility needs within the organization. These platforms typically include application management, content management, and advanced identity management, making them ideal for organizations with complex security and compliance demands.
The components of EMM solutions and their capabilities are Artikeld in the following table:
| Component | Description | Security Features | Integration Capabilities |
|---|---|---|---|
| Device Management | Core enrollment, provisioning, and policy enforcement for devices | Encryption enforcement, remote lock/wipe | Directory services, network access controls |
| Application Management | Distribution, configuration, and updating of apps | App containerization, app-level VPN | App stores, enterprise portals |
| Content Management | Secured access and sharing of corporate content | Data loss prevention, document encryption | Cloud storage, file servers |
| Identity and Access Management | Authentication and user access controls | Multi-factor authentication, single sign-on | SSO with enterprise apps, integration with IAM solutions |
Unified Endpoint Management (UEM) Systems
UEM represents the next evolution in device management. While MDM and EMM primarily focus on mobile devices, UEM platforms manage all types of endpoints in an organization, including mobile devices, desktops, laptops, and even IoT devices, through a single console. UEM systems streamline management processes and improve visibility and security across the entire device landscape.
Examples of leading UEM systems include:
- VMware Workspace ONE
- Microsoft Endpoint Manager (Intune + Configuration Manager)
- IBM Security MaaS360 with Watson
- Ivanti UEM
Primary use cases for UEM solutions involve organizations seeking holistic management for diverse device environments, especially those supporting remote workforces, mixed OS deployments, and advanced automation for endpoint compliance.
Comparing UEM to legacy management approaches:
- UEM provides a single pane of glass for all device types, reducing complexity and administrative overhead.
- Legacy MDM/EMM required separate tools for desktops and mobile devices, often resulting in policy gaps.
- UEM supports deeper automation, analytics, and integration, allowing better response to security incidents.
- Organizations benefit from unified policy enforcement across mobile and non-mobile endpoints.
Key Procedures in Centralized Device Administration
Effective centralized device management begins with precise procedures for enrolling devices and maintaining compliance. These processes ensure that every device accessing the organization’s resources adheres to established security and operational standards.
Device enrollment typically follows these steps:
- IT creates or configures enrollment profiles within the central management console.
- Users receive an invitation or are prompted to download a management app or profile.
- Device authentication occurs, often requiring user credentials or multi-factor authentication.
- The management profile is installed, granting the system control over specified device settings.
- Compliance checks and baseline configurations are automatically applied.
To set up automated device compliance policies, administrators generally perform these steps:
- Define compliance rules (e.g., minimum OS version, password requirements, encryption enabled).
- Configure automated actions for non-compliant devices (e.g., restrict access, send alerts, initiate device wipe).
- Schedule regular compliance checks and automate reporting.
- Communicate policy requirements to users and provide support channels for remediation.
Security Features in Centralized Mobile Device Software
One of the core strengths of centralized device management software is its ability to enforce comprehensive security controls across all managed endpoints. These features protect sensitive data, ensure regulatory compliance, and reduce the risk of breaches.
The following table summarizes key security features commonly found in centralized mobile device management software:
| Feature | Function | Benefit | Applicable Device Types |
|---|---|---|---|
| Remote Wipe | Erase all data from lost or stolen devices | Prevents data loss and unauthorized access | Mobile, Tablets, Laptops |
| Encryption Enforcement | Ensures device storage is encrypted | Secures sensitive data at rest | Mobile, Tablets, Desktops |
| Access Restrictions | Limits access to corporate resources based on compliance | Reduces attack surface, ensures only trusted devices connect | All managed endpoints |
| Application Control | Whitelist or blacklist certain apps | Prevents use of risky or unauthorized apps | Mobile, Tablets |
| Network Configuration | Automates VPN and Wi-Fi profiles | Secures network connections, enforces safe access | Mobile, Laptops |
Integration Capabilities with Other Enterprise Systems
Centralized administration solutions often need to work seamlessly with other enterprise IT systems to maximize security and efficiency. Integration ensures that device policies align with user identities, email systems, and broader IT management frameworks.
Integration typically involves connecting the device management console to:
- Identity and access management systems (like Active Directory, Azure AD)
- Email and messaging servers (such as Microsoft Exchange or Google Workspace)
- Security information and event management (SIEM) platforms
- Help desk and IT service management tools
The procedures for enabling these integrations usually include configuring connectors, establishing trust relationships, synchronizing user and device directories, and setting up automated workflows for provisioning and deprovisioning. The primary benefits are streamlined user onboarding/offboarding, consistent security policies, and centralized monitoring of device and user activity.
Use Cases and Industry Applications
Centralized mobile device administration is essential for sectors where data protection, regulatory compliance, and operational efficiency are critical. Below are scenarios that illustrate how different industries leverage these solutions:
A large healthcare provider utilizes a UEM platform to manage both company-owned tablets for clinicians and BYOD smartphones for administrative staff. By enforcing encryption, automated OS updates, and remote wipe capabilities, the organization ensures HIPAA compliance and patient data protection. Rapid enrollment and automated compliance reporting free up IT resources and improve clinical workflow efficiency.
In education, a public school district rolls out MDM across thousands of student tablets and teacher laptops. Automated device enrollment, app whitelisting, and content filtering features enable the district to support remote learning while ensuring student safety and compliance with legal standards like COPPA and FERPA.
A global financial services firm implements EMM to enable secure mobile banking operations for its employees. Advanced identity management and containerized apps allow staff to securely access sensitive client data on personal devices, with the ability to revoke access instantly if a device is compromised.
Best Practices for Implementing Centralized Administration Software, Which type of software enables centralized administration of mobile devices
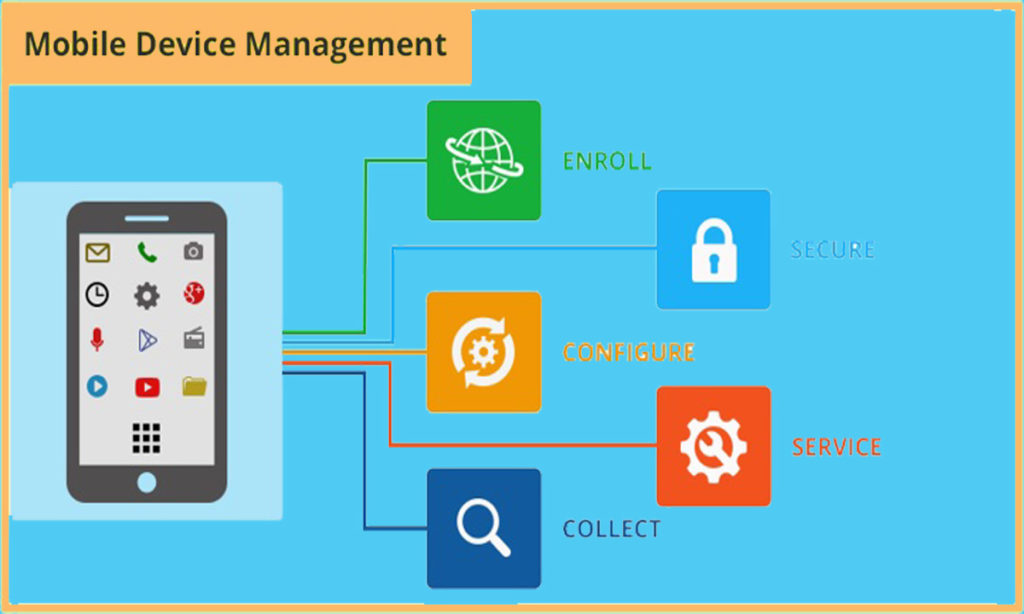
Deploying centralized device management software requires careful planning and a strategic approach. The following step-by-step guide supports a successful deployment:
- Assess organizational needs and define device management objectives.
- Evaluate and select a solution that aligns with device types, compliance requirements, and integration needs.
- Develop detailed policies for device usage, security, and user privacy.
- Pilot the software with a small group of users to identify potential issues and gather feedback.
- Roll out the solution organization-wide with clear communication and user training.
- Monitor device compliance and security continuously, adapting policies as needed.
- Regularly review integration points and update them to support evolving business processes.
Organizational policies should include clear guidelines on acceptable device usage, incident reporting procedures, data security standards, and employee responsibilities. Involving stakeholders from IT, HR, legal, and relevant business units ensures policies are comprehensive and enforceable.
Conclusion
In conclusion, understanding which type of software enables centralized administration of mobile devices empowers organizations to stay ahead of security threats, manage assets efficiently, and support a mobile workforce with confidence. By choosing the right solution and following best practices, businesses can unlock smoother operations and superior protection for every device, setting the stage for greater productivity and peace of mind.
Query Resolution
What are the main benefits of centralized mobile device administration?
Centralized administration simplifies device management, improves security, reduces IT workload, and ensures consistent policy enforcement across all devices.
Is centralized device management only for large organizations?
No, businesses of all sizes can benefit from centralized device management, as it offers scalability and flexibility tailored to diverse organizational needs.
Can these solutions manage devices from different manufacturers?
Yes, most modern solutions support a wide range of device brands and operating systems, making them suitable for mixed-device environments.
How do these platforms enhance security?
They provide features like remote wipe, encryption, policy enforcement, and real-time monitoring to protect sensitive data and prevent unauthorized access.
Is it difficult to integrate centralized device management with existing IT infrastructure?
Most solutions are designed with integration in mind, offering connectors for identity management, email servers, and other enterprise applications to enable a seamless experience.
