Enabled software opens new horizons for organizations by providing advanced capabilities that go beyond traditional applications. It paves the way for smarter workflows, seamless integrations, and intelligent automation, making it a driving force behind digital transformation in today’s business landscape.
At its core, enabled software refers to solutions that are purpose-built to connect, automate, and enhance existing systems, typically through features like real-time data exchange, customizable modules, and cloud integration. These solutions cater to diverse industries and user needs, offering not just tools, but powerful platforms that adapt and scale with changing technology and business demands.
Definition and Core Features of Enabled Software
Enabled software refers to applications and platforms designed to extend conventional software functionality through enhanced automation, integration, and adaptability. Typically, enabled software leverages technologies such as APIs, machine learning, or cloud connectivity to support dynamic business processes and improve user experience. What distinguishes enabled software from standard applications is its capacity to interact seamlessly with other systems, self-optimize, and provide context-aware functionalities that adapt to user or environmental needs.
Enabled software solutions are recognized by features that go beyond static workflows or standalone operations. They are developed to be responsive, interoperable, and scalable, facilitating more intelligent decision-making and efficient process automation.
Distinguishing Characteristics of Enabled Software
Key differentiators set enabled software apart from traditional applications by emphasizing adaptability, integration, and continuous improvement. This enhanced capability allows organizations to future-proof their operations and respond to evolving market demands. The following points provide a comprehensive overview of the typical functionalities present in enabled software:
- Automated data synchronization across multiple platforms or devices
- Integration with third-party tools via open APIs or middleware
- Real-time analytics and reporting powered by advanced algorithms
- Context-aware operations adapting to user preferences or locations
- Scalable architecture supporting cloud and hybrid deployments
- Role-based access control and enhanced security measures
- Remote management and monitoring capabilities
Enabled software transforms static tools into dynamic, interactive systems capable of adapting to changing organizational needs.
Types and Categories of Enabled Software
Enabled software spans a wide range of categories across diverse industries, each addressing unique operational challenges and delivering tailored value. The categorization of enabled software helps organizations select solutions that align with their business objectives, regulatory requirements, and user expectations.
Categories and Industry Examples of Enabled Software
Different types of enabled software are designed to meet specific requirements in various sectors, from workflow automation to smart manufacturing. The table below summarizes key categories, providing descriptions, typical use cases, and notable examples for reference.
| Category | Description | Typical Use Cases | Notable Examples |
|---|---|---|---|
| Workflow Automation | Automates repetitive business processes and tasks | Invoice approvals, document routing, HR onboarding | UiPath, Zapier, Microsoft Power Automate |
| Integration Platforms | Facilitates connectivity between disparate systems | ERP-CRM data exchange, cloud storage sync | MuleSoft, Dell Boomi, Apache Camel |
| Smart Analytics | Extracts actionable insights from large datasets | Sales forecasting, fraud detection, performance dashboards | Tableau, Power BI, Splunk |
| IoT Management | Controls and monitors connected devices in real time | Asset tracking, predictive maintenance, energy monitoring | AWS IoT Core, PTC ThingWorx |
| AI-Enabled Software | Incorporates AI/ML models for intelligent operations | Chatbots, personalized recommendations, anomaly detection | IBM Watson, Google Cloud AI, Salesforce Einstein |
Each category addresses distinct business or user needs, such as automating manual processes in finance, improving customer service with AI, or streamlining manufacturing operations with IoT-enabled platforms. By aligning enabled software with industry demands, organizations can optimize efficiency, reduce errors, and unlock new opportunities for innovation.
Technical Foundations and Integration Methods
The technical infrastructure behind enabled software is engineered to support scalable, secure, and high-performance operations. These solutions often utilize cloud-native architectures, microservices, RESTful APIs, and robust middleware to enable real-time data exchange and modular functionality. Underlying frameworks ensure that enabled software can integrate seamlessly into complex IT environments without causing significant disruptions.
Underlying Technologies Powering Enabled Software
Enabled software relies on a stack of modern technologies to deliver its advanced features. These technologies are selected for their robustness, flexibility, and ability to support high levels of connectivity and automation. Organizations benefit from adopting these foundations, as they ensure future scalability and compatibility with emerging tools.
- Cloud Computing and Virtualization: Supports elastic scaling and remote accessibility
- Microservices Architecture: Enables modular, independently deployable components
- RESTful APIs and GraphQL: Facilitates efficient data exchange and integration
- Machine Learning Libraries: Powers intelligent analytics and adaptive features
- Containerization (Docker, Kubernetes): Ensures consistent deployment across environments
- Middleware Platforms: Bridges legacy and modern systems
Integration with Existing IT Infrastructure
Integrating enabled software with legacy or cloud-based IT systems requires careful planning and execution. The integration process typically involves mapping data flows, setting up secure connectors, and ensuring compatibility with existing applications. Well-executed integration helps preserve data integrity, minimizes downtime, and accelerates value realization.
Step-by-Step Procedure for Implementing Enabled Software in Enterprise Environments
Implementing enabled software within a large organization benefits from a disciplined, phased approach. The following steps Artikel a recommended procedure to ensure smooth deployment and rapid user adoption:
- Conduct a comprehensive requirements analysis involving all stakeholders
- Assess the compatibility of enabled software with current IT infrastructure
- Develop a detailed integration plan, including data mapping and security considerations
- Set up sandbox or test environments to validate integration points
- Execute phased deployment, starting with pilot teams or departments
- Monitor system performance and gather user feedback for iterative improvements
- Train end users and administrators to maximize adoption and proficiency
- Document procedures, configurations, and troubleshooting guidelines
By leveraging robust technical foundations and structured integration methods, enabled software can transform enterprise operations into more responsive and scalable systems.
Benefits and Challenges
Organizations adopting enabled software stand to gain significant competitive advantages, including improved workflow efficiency, enhanced data insights, and greater scalability. However, deploying these solutions is not without its challenges—issues such as integration complexity, data security, and user training must be addressed to achieve successful outcomes.
Benefits and Challenges of Enabled Software Adoption
The following table Artikels the key benefits and challenges organizations may encounter, along with their respective impacts, example scenarios, and strategies to mitigate potential risks.
| Benefit/Challenge | Impact | Example Scenario | Mitigation Strategy |
|---|---|---|---|
| Enhanced Workflow Automation | Reduces manual workload and error rates | Automated invoice processing shortens payment cycles | Standardize process templates and automation rules |
| Seamless Integration | Improves data sharing and collaboration | CRM and ERP systems exchange real-time customer data | Invest in robust middleware and API management |
| Scalability and Flexibility | Enables rapid adaptation to business growth | Cloud deployment scales resources during peak demand | Design for modular expansion and elastic provisioning |
| Integration Complexity | Potential for increased setup time and technical debt | Legacy system requires significant refactoring | Conduct thorough pre-implementation assessments |
| Data Security Concerns | Risk of breaches or compliance violations | Sensitive HR data exposed via misconfigured API | Enforce access controls and routine security audits |
| User Training and Change Management | Delays in user adoption and productivity gains | End users struggle with new interface features | Develop role-based training programs and support |
Common Use Cases and Industry Applications

Enabled software drives transformation in a variety of industry sectors by streamlining workflows, improving decision-making, and enhancing customer engagement. Its versatility allows for adaptation to specific regulatory, operational, and user requirements, making it a key driver of innovation.
Industry Applications of Enabled Software
The following table summarizes prominent use cases of enabled software across several major industries, describing the specific application, resulting outcomes, and key features enabled by these solutions.
| Industry | Application | Outcome | Key Features Enabled |
|---|---|---|---|
| Healthcare | Remote patient monitoring using IoT-enabled devices | Early intervention and continuous care for chronic conditions | Real-time data analytics, secure remote access, automated alerts |
| Finance | Fraud detection powered by AI-enabled analytics | Reduced financial losses and improved regulatory compliance | Machine learning, automated transaction flagging, risk scoring |
| Education | Adaptive learning platforms for personalized instruction | Higher student engagement and improved learning outcomes | Personalization engines, real-time feedback, scalable content delivery |
| Manufacturing | Predictive maintenance via IoT sensors | Minimized downtime and optimized equipment usage | Sensor data integration, predictive analytics, automated scheduling |
Enabled software not only optimizes workflows but also creates entirely new business models, such as telemedicine in healthcare or real-time supply chain management in manufacturing. These practical applications demonstrate how enabled software can be a catalyst for operational excellence and strategic growth.
Security and Compliance Considerations: Enabled Software
Security and compliance are fundamental to the successful deployment of enabled software, especially as organizations increasingly rely on interconnected systems and process sensitive data. Addressing these aspects involves implementing robust security protocols, ensuring regulatory compliance, and continuously monitoring for vulnerabilities.
Security Measures and Protocols in Enabled Software
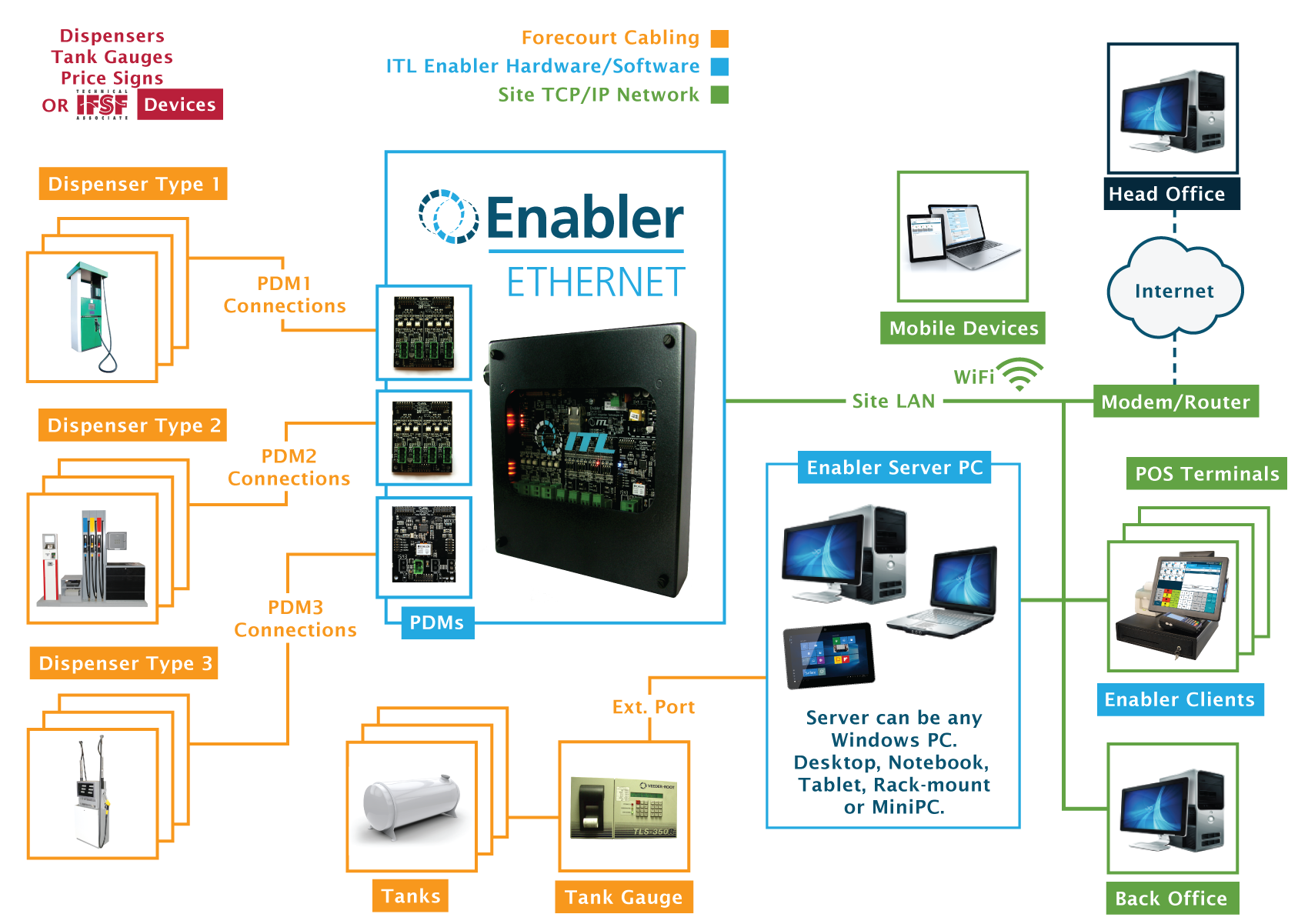
Enabled software must adhere to stringent security standards to protect organizational assets and user data. Security mechanisms are designed to prevent unauthorized access, detect anomalies, and respond to potential threats in real time.
- Multi-factor authentication (MFA) for access control
- End-to-end data encryption in transit and at rest
- Automated security event monitoring and alerting
- Regular vulnerability scanning and patch management
- Role-based permissions and least-privilege access models
Compliance Requirements Across Regions and Industries
Compliance considerations vary depending on the region and industry sector, with regulations such as GDPR in Europe, HIPAA in the United States, or PCI DSS in the financial sector. Organizations must align their enabled software deployments with relevant legal and regulatory frameworks to avoid penalties and ensure trust.
Best Practices for Data Protection with Enabled Software
Implementing best practices is essential for maintaining the confidentiality, integrity, and availability of data processed by enabled software solutions.
- Regularly review and update privacy policies and user consent documentation
- Conduct routine compliance audits and security assessments
- Segregate sensitive data and apply strict data retention policies
- Train employees on cybersecurity awareness and compliance requirements
- Establish incident response plans for rapid threat mitigation and communication
Concluding Remarks
As we’ve explored, enabled software is shaping the future of how organizations operate, innovate, and stay competitive. With the right strategy, careful evaluation, and a focus on user experience, businesses can leverage enabled software to maximize efficiency, ensure security, and unlock unprecedented value in the digital era.
Frequently Asked Questions
What is enabled software?
Enabled software is a type of application or platform designed to integrate seamlessly with other systems, automate workflows, and provide enhanced features that traditional software may lack.
How does enabled software differ from regular software?
Enabled software typically offers greater flexibility, connectivity, and scalability, allowing organizations to customize, automate, and optimize processes more effectively than with standard applications.
Can enabled software be used by small businesses?
Yes, there are many enabled software solutions tailored for businesses of all sizes, including small and mid-sized companies seeking to modernize their operations.
Is special training required to use enabled software?
While some solutions may require user training or onboarding, many enabled software platforms are designed with intuitive interfaces and offer support resources to help users get started quickly.
How secure is enabled software?
Enabled software often includes robust security measures such as encryption, access controls, and compliance features, but organizations should always assess security protocols before implementation.
